Penetration Testing Checklist
On this page, you will find the Penetration Testing Checklist. It is by no means exhaustive and is to be regularly updated.
Last updated on: 2022-06-07
Table of contents
Open-source intelligence
Penetration Testing Checklist: OSINT – Domain
Whois – retrieve WHOIS records for domains within scope. Can be done with the whois utility on the Linux command line or by using 3rd party websites (who.is). Can reveal useful information about the domain registrant.
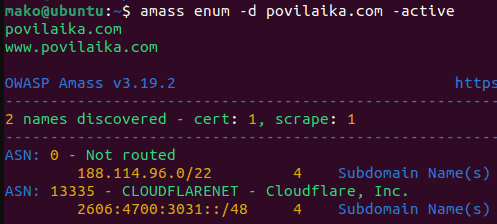
Subdomain discovery – find all subdomains for the target domain without interacting with it. Can be done with tools like Amass and sublist3r. 3rd party websites like SecurityTrails may provide relevant historical information.
Google dorking – find relevant information using search engines. A collection of search terms (“dorks”) for this task can be found on Google Hacking Database by Offensive Security. Manual Google searching or automated tools such as pagodo can be used.
Certificate research – find current and historical certificate information. Often useful in revealing the original IP addresses behind CDNs. 3rd party websites are the preferred way of approach (crt.sh).
Contact discovery – retrieve contact information (such as email addresses) related to a domain. Self-hosted passive OSINT tools such as theHarvester can be used, as well as 3rd party websites like Hunter.
Penetration Testing Checklist: OSINT – IP address
Reverse DNS lookups – find domains associated with the IP address. Command-line utilities such as host, dig, or nslookup can be used.
Specialized search engine search – specialized search engines (such as Shodan or Censys) can be used to find information about IP addresses without actively probing them.
Penetration Testing Checklist: OSINT – Email address
Breach data lookups – websites like Have I Been Pwned can be used to find information about the presence of an email address in public data breaches. Paid 3rd party services like DeHashed and Intelligence X can also provide the data from within the breaches.
Automated tools – automated email passive reconnaissance tools like MOSINT or GHunt can also provide valuable information.
Enumeration
Penetration Testing Checklist: Enumeration – Domain
Subdomain brute-forcing – discover subdomains by fuzzing the target domain. Tools such as dnsrecon can be used for this task.
Virtual host (vhost) brute-forcing – find virtual hosts on a target server. The tool GoBuster with SecLists, fuzzdb, or other publicly available wordlists can be used to accomplish this.
Zone transfer enumeration – abuse zone transfer vulnerability on misconfigured domains to reveal additional DNS records. Can be done with tools such as dnsenum.
Penetration Testing Checklist: Enumeration – IP address
Port scanning – discover open ports on a remote host. Some of the commonly used tools to accomplish this task are nmap, masscan, and RustScan.
Service enumeration/banner grabbing – a technique related to port scanning. Reveals running services and their versions on open ports. Usually done with nmap.
OS detection – detect the operating system a host is running. Also done with nmap.
Penetration Testing Checklist: Enumeration – Web content
Directory brute-force – brute-force files and directories on the target web server. Can be done with tools such as ffuf, dirb, or GoBuster.
Spider scraping – a more intelligent alternative (or supplement) to traditional directory brute-forcing. Done with tools called ‘spiders’, such as GoSpider.
Technology fingerprinting – a technique used to detect technologies present on a target website. A tool like whatweb automates this.
Vulnerability assessment
Penetration Testing Checklist: Vulnerability assessment – General
Nmap scripts – vulnerability assessment can be done using nmap’s NSE scripts. They can be found at /usr/share/nmap/scripts.
Metasploit modules – The Metasploit Framework has a large collection of modules to check for specific vulnerabilities.
Vulnerability scanners – these tools try to automatically identify vulnerabilities on a given target. Popular examples are Nessus (commercial, but has a free ‘Essentials’ edition) and OpenVAS (free and open-source).
Manual searching – a manual technique for finding vulnerabilities on targets. Usually done by researching known software versions (for example, a specific WordPress plugin version). Exploit-DB and Vulners websites are a good starting point.
Penetration Testing Checklist: Vulnerability assessment – Web server
Vulnerability scanning – on top of traditional vulnerability scanners, web server-specific scanners like Nikto or Metasploit’s WMAP can be used.
Checking security headers – make sure to inspect security headers on the target to reveal HTTP daemon configuration issues. Tools like shcheck automate the process.
Testing SSL/TLS configuration – use tools like testssl.sh to find SSL/TLS-related vulnerabilities in web servers that use HTTPS.
Penetration Testing Checklist: Vulnerability assessment – Web application
Web vulnerability scanning – done by using vulnerability scanners built specifically for auditing web applications. Commercial examples are Burp Suite and Acunetix, open-source – OWASP Zap and SkipFish.
Specialized web application vulnerability scanning – specialized tools like joomscan and wpscan often provide better results than general web vulnerability scanners.
Exploitation
The exploitation phase is different for every engagement. If traditional approaches do not work, research the CVE entry, source code, vendor advisory, or the type of vulnerability you are trying to exploit.
Penetration Testing Checklist: Exploitation – General
General exploitation frameworks – use pre-made tools and frameworks like Metasploit or Armitage (GUI for Metasploit) to exploit vulnerable targets.
Specialized exploitation frameworks – use tools like BeEF Framework, sqlmap or commix to exploit specific vulnerability classes.
Manual exploitation – exploitation using manually acquired exploits from repositories like Exploit-DB or Packet Storm.
Reporting
Automated vulnerability assessment tools are often shipped with reporting capabilities.
Penetration Testing Checklist: Reporting – General
Note taking applications – note taking applications like Notion or CherryTree can export your notes into formats like PDF while retaining their hierarchy.
Open-source reporting frameworks – free and open-source frameworks like Dradis-CE can be used to report your findings with pre-made templates.
Commercial reporting frameworks – notably the Penetration Testing Workshop.
Manual reporting – reporting can be always done with office software like Microsoft Word or LibreOffice Writer.